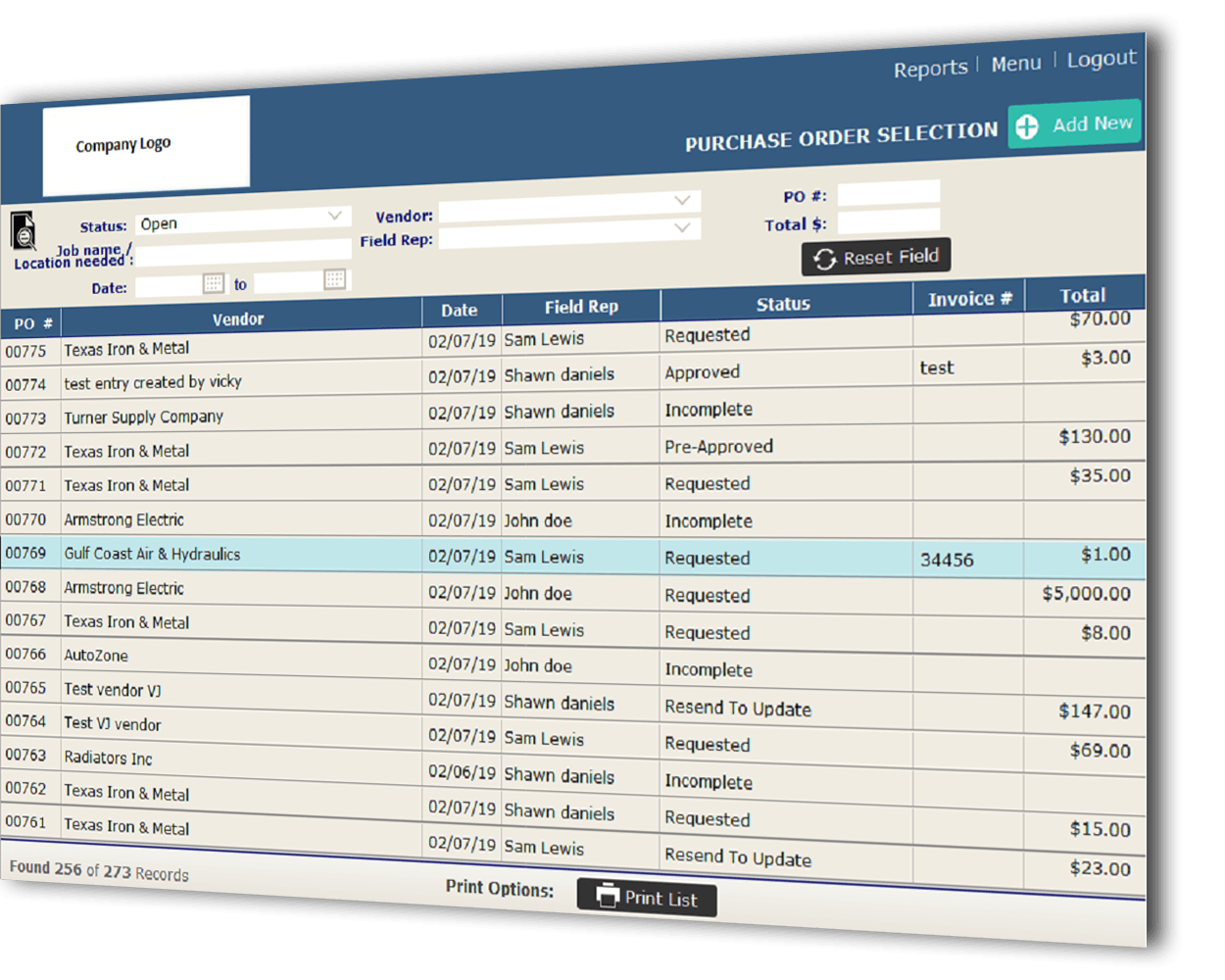
As businesses increasingly rely on digital platforms for procurement, it’s essential to address the security implications associated with online purchase order systems. From data breaches to cyberattacks, the risks are manifold, requiring proactive measures to safeguard critical information and maintain trust among stakeholders.
This article aims to provide businesses with insights into the security considerations relevant to online purchase order systems, empowering them to navigate the security landscape effectively and protect their assets from potential threats.
Understanding the Security Risks
Online purchase order systems are susceptible to various security risks that can compromise the confidentiality, integrity, and availability of data. Some of the common risks include:
- Data Breaches: Unauthorized access to sensitive information, such as vendor details, pricing agreements, and payment details, can result in data breaches, leading to financial losses and reputational damage.
- Phishing Attacks: Phishing emails disguised as legitimate communication from vendors or colleagues can trick users into disclosing login credentials or sensitive information, posing a significant security threat.
- Malware Infections: Malicious software, such as ransomware and keyloggers, can infect the systems hosting online purchase order systems, allowing attackers to steal data or disrupt operations.
- Insider Threats: Employees with access to the purchase order system may intentionally or unintentionally compromise security by sharing login credentials, mishandling data, or engaging in malicious activities.
Understanding these risks is the first step towards developing a comprehensive security strategy to protect online purchase order systems from potential threats.
Moreover, the threat landscape is continually evolving, with cybercriminals employing sophisticated tactics to exploit vulnerabilities. Therefore, businesses must remain vigilant and proactive in addressing emerging threats to safeguard their purchase order systems.
Best Practices for Securing Purchase Order Systems
Implementing robust security measures is essential to mitigate the risks associated with online purchase order systems. Here are some best practices:
- Access Control: Implement role-based access control to restrict access to sensitive data and functionalities based on user roles and responsibilities.
- Encryption: Encrypt data transmission and storage to prevent unauthorized access and ensure the confidentiality of information exchanged within the purchase order system.
- Multi-factor Authentication: Enforce multi-factor authentication to add an extra layer of security, requiring users to provide additional verification beyond passwords to access the system.
- Regular Updates and Patch Management: Keep the purchase order system and associated software up to date with the latest security patches and updates to address known vulnerabilities and protect against emerging threats.
- Employee Training: Provide comprehensive training to employees on security best practices, including how to identify and respond to phishing attempts, safeguard login credentials, and report suspicious activities.
- Monitoring and Incident Response: Implement continuous monitoring mechanisms to detect anomalous activities and security incidents in real-time, enabling prompt response and mitigation.
By adopting these best practices, businesses can enhance the security posture of their online purchase order systems and mitigate potential risks effectively.
Furthermore, establishing a robust incident response plan is essential for effectively managing security incidents and minimising their impact on business operations. This plan should outline clear procedures for incident detection, response, containment, and recovery, ensuring a swift and coordinated response to security breaches.
Integration with Security Solutions
Another crucial aspect of securing online purchase order systems is integrating them with dedicated security solutions and services. These may include:
- Firewalls and Intrusion Detection Systems (IDS): Deploy firewalls and IDS to monitor network traffic and detect and block suspicious activities or unauthorized access attempts.
- Endpoint Security Solutions: Install endpoint security software on devices accessing the purchase order system to protect against malware, phishing, and other threats.
- Security Information and Event Management (SIEM): Implement SIEM solutions to centralize and analyse security logs and events from various sources, enabling proactive threat detection and response.
- Vulnerability Management: Utilise vulnerability management tools to identify and remediate security vulnerabilities in the purchase order system and associated infrastructure.
Integrating online purchase order systems with these security solutions enhances their resilience against cyber threats and strengthens the overall security posture of the organisation.
Moreover, businesses should regularly assess the effectiveness of their security measures through comprehensive security audits and penetration testing. These assessments help identify potential vulnerabilities and weaknesses in the purchase order system, allowing businesses to address them proactively before they can be exploited by malicious actors.
Ultimately, investing in the security of online purchase order systems is not just a defensive measure; it’s a strategic imperative for businesses looking to thrive in an increasingly interconnected and digitised world. By prioritising security and adopting a proactive approach to threat mitigation, businesses can ensure the integrity, confidentiality, and availability of their purchase order systems, thereby driving operational efficiency and maintaining a competitive edge in the market.